Protect your iPhone from Trustjacking – iOS Vulnerability: Have you ever thought that connecting to a free charging port at an Airport Terminal can leave your iPhone’s data exposed to hackers even when you have disconnected? After reading this post you may think multiple times for connecting your iPhone to even your friend’s computer. In this post we are going to talk about an iOS vulnerability called ‘Trustjacking’ which has been recently discovered by security experts at Symantec.
Contents
What is Trustjacking? How does it work?
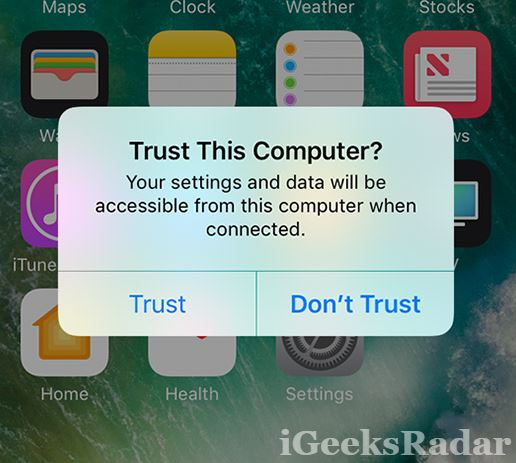
Trustjacking misuses the iTunes WiFi Sync Feature through which an iOS user synchronizes their iPhone with iTunes without connecting to the PC. We all connect our iPhone through USB Data Cable and ‘Trust’ the computer. We perform multiple things thereafter like access photographs, add videos or music, take backup and do multiple things with the assistance of iTunes. Also, this permits us to activate the ‘iTunes WiFi Sync‘ feature through which we needn’t connect our iPhone to the PC later for performing the same things as mentioned above.
The thing to be observed here is that activating ‘iTunes WiFi Sync’ can be done from the PC. This doesn’t require any kind of approval from us since we have already trusted the computer. So, whenever we are trusting a malicious computer or even a free charging port, a hacker can easily gain remote access to our device through ‘iTunes WiFi Sync’ feature.
A hacker needs to do only two things in the time frame when our iOS device is connected to the malicious computer or port. Connect the device to iTunes and enable iTunes WiFi Sync. These steps can be easily automated and done in a jiffy. Moreover, we don’t even get any information on our iPhone that ‘iTunes WiFi Sync‘ has been activated. So, we might think that when we have disconnected our iPhone nobody can access it. But, as long as we and the hacker are in same network, the hacker can remotely control our iOS device.
Trustjacking | What a Hacker can do with our iPhone?
Just tapping that one ‘Trust’ button can make us a victim of a Trustjacking attack. A hacker can see live as to what we are doing on our iPhone. Plus a hacker can also get access to our photographs, SMS /iMessage History and even App Data. For this a hacker requires utilizing the feature of remote iTunes backup.
Moreover, a hacker can install malicious applications on our iPhone. He can also replace the existing ones with an altered version. These replaced applications look and work just like the original application.
Trustjacking | Is Trustjack attack limited to WiFi?
Since, the Trustjack attack requires the victim and the hacker to be in the same network, we might think that when we are not connected to the same WiFi we are safe.
But, this is not the case as a hacker can actually use the malicious profile attack and connect the iOS device to a VPN Server. This way a persistent connection is created. The hacker can exploit our iPhone anytime without needing the device to be connected to the same network.
Apple did add the ‘Pass Code‘ feature i.e. whenever we are trusting a computer or a port we need to enter our Pass Code . This doesn’t help in case of Trustjacking.
Moreover, Our own PC or MAC can be infected by a malware. This way, a hacker can not only access our activities on the computer but also on your iOS device. A hacker doesn’t even needs to be close by for this.
So, what are the steps that you can take to protect your iPhone from Trustjack attacks? Read below to find out.
Must Read: BioProtect X: Protect Apps with Face ID & Touch ID on iOS [Tutorial].
Steps to Secure your iPhone from Trustjacking
Reverse & Overturn Access to Trusted Computers
- Break the connection between your iPhone and the malicious computer.
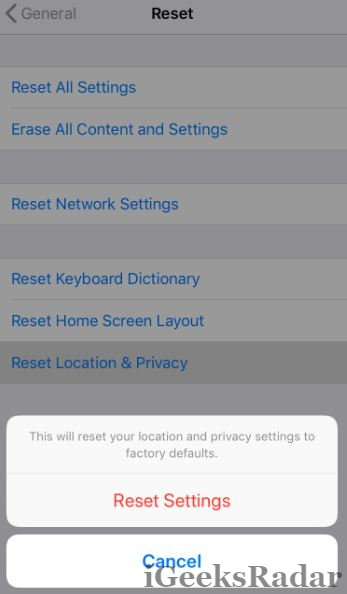
- Navigate to Settings -> General -> Reset
- Please click on ‘Reset Location & Privacy.’
- We require entering our pass code to provide confirmation for the same.
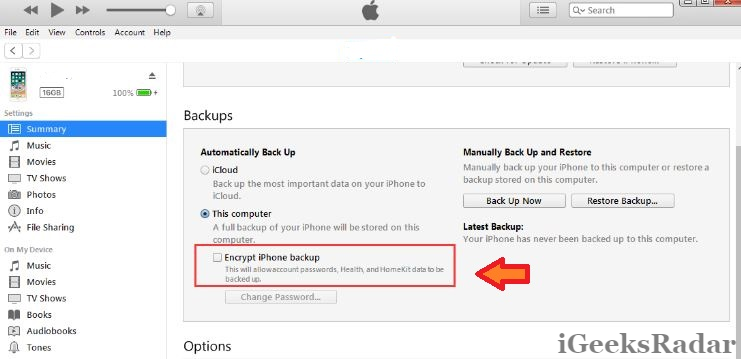
Encrypting iPhone Backups
- Encrypting data is considered essential to stop a hacker from accessing your data even if the hacker has managed to retrieve it.
- We can encrypt our iPhone’s backup from iTunes. We need to select the option of ‘Encrypt iPhone Backup.’ Keeping a strong password for this is essential.
Installation of SEP Mobile Application
- Security Applications can be installed to keep our iPhone safe and secure from malicious profiles and apps. SEP Mobile Application has been vouched by the Symantec Security Team.
- The application can be downloaded from the App Store.
These are the ways through which we can protect our iPhone from Trustjacking attacks.
You may like to read the following posts:
- iOS 11.2.6 Jailbreak: KASLR Bypass Tool for iOS 11.2.6.
- iOS 11.3 Jailbreak: Latest 0day Bug might lead to JailBreak.